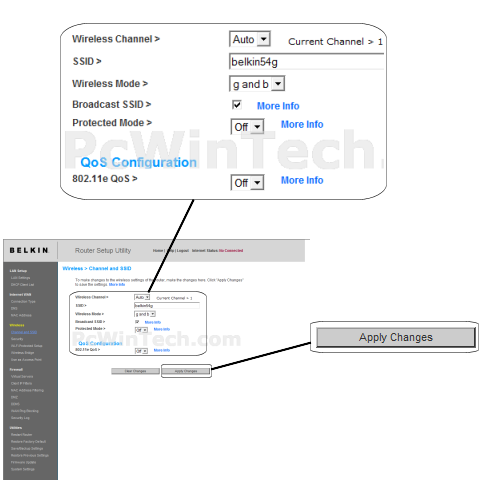
F5D9630-4 ADSL2+ Modem with Wireless G Plus MIMO Router User Manual P75125uk_F5D9630ukcoverchange.indd Belkin .

Belkin F5D9630-4 ADSL2+ Modem with Wireless G Plus MIMO Router- No Power Supply | Switches/Routers | Blackmore IT

Best Buy: Belkin Wireless-G Plus MIMO Router with USB Adapter and Geek Squad® Installation B5D-045-GS